The Attack
The Attack Level & Response
The Attacker & Victim's OS
> Some Forms <
A firewall is any device used to prevent outsiders from gaining access to your network. This device is usually a combination of software and hardware. Firewalls commonly implements exclusionary schemes or rules that sort out wanted and unwanted addresses.
The most fundamental components of a firewall exist neither a hardware nor software, but inside the mind of the person construct it. A firewall, as its conception, is a concept rather than a product. It is an idea in the architect’s mind of who and what will be allowed into the network. Who and what dramatically influence the network traffic is routed. For this reason, construct firewall is part art, part common sense, part ingenuity, and part logic.
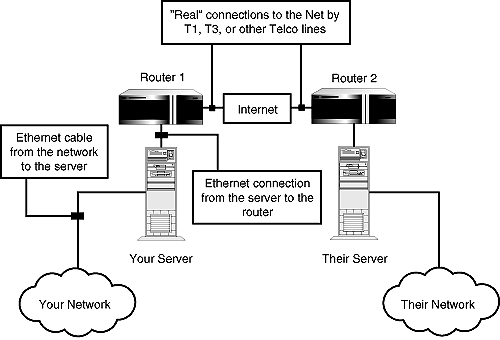
Firewall can be composed of software, or hardware, or both. But in any event, all firewalls share a common attribute: the capability to discriminate or the capability to deny access generally based on source address.
Resources
Internet Firewalls and Network Security (Second Edition). Chris Hare and Karanjit Siyan. New Riders. ISBN: 1-56205-632-8. 1996.
Internet Firewalls. Scott Fuller and Kevin Pagan. Ventana Communications Group Inc. ISBN: 1-56604-506-1. 1997.
Building Internet Firewalls. D. Brent Chapman and Elizabeth D. Zwicky. O'Reilly & Associates. ISBN: 1-56592-124-0. 1995.
Firewalls and Internet Security : Repelling the Wily Hacker. William R. Cheswick and Steven M. Bellovin. Addison-Wesley Professional Computing. ISBN: 0-201-63357-4. 1994.
Actually Useful Internet Security Techniques. Larry J. Hughes, Jr. New Riders. ISBN: 1-56205-508-9. 1995.
Internet Security Resource Library: Internet Firewalls and Network Security, Internet Security Techniques, Implementing Internet Security. New Riders. ISBN: 1-56205-506- 2. 1995.
Firewalls FAQ. Marcus J. Ranum.
NCSA Firewall Policy Guide. Compiled by Stephen Cobb, Director of Special Projects. National Computer Security Association.
Comparison: Firewalls. Comprehensive comparison of a wide variety of firewall products. LANTimes. June 17, 1996.
There Be Dragons. Steven M. Bellovin. Proceedings of the Third Usenix UNIX Security Symposium, Baltimore, September 1992. AT&T Bell Laboratories, Murray Hill, NJ. August 15, 1992.
Rating of Application Layer Proxies. Michael Richardson.
Keeping Your Site Comfortably Secure: An Introduction to Internet Firewalls. John P. Wack and Lisa J. Carnahan. National Institute of Standards and Technology.
SQL*Net and Firewalls. David Sidwell and Oracle Corporation.
Covert Channels in the TCP/IP Protocol Suite. Craig Rowland. Rotherwick & Psionics Software Systems Inc.
If You Can Reach Them, They Can Reach You. William Dutcher. A PC Week Online Special Report, June 19, 1995.
Packet Filtering for Firewall Systems. February 1995. CERT (and Carnegie Mellon University).
Network Firewalls. Steven M. Bellovin and William R. Cheswick. IEEECM, 32(9), pp. 50-57, September 1994.
Session-Layer Encryption. Matt Blaze and Steve Bellovin. Proceedings of the Usenix Security Workshop, June 1995.
A Network Perimeter With Secure External Access. Frederick M. Avolio and Marcus J. Ranum. An extraordinary paper that details the implementation of a firewall purportedly at the White House.
Packets Found on an Internet. Steven M. Bellovin. Lambda. Interesting analysis of packets appearing at the application gateway of AT&T.
Using Screend to Implement TCP/IP Security Policies. Jeff Mogul. Rotherwick and Digital.
Firewall Application Notes. Livingston Enterprises, Inc. Good document that starts by describing how to build a firewall. It also addresses application proxies, Sendmail in relation to firewalls, and the characteristics of a bastion host.
X Through the Firewall, and Other Application Relays. Treese/Wolman. Digital Equipment Corp. Cambridge Research Lab.
Intrusion Protection for Networks 171. BYTE Magazine. April, 1995.
Benchmarking Methodology for Network Interconnect Devices (RFC 1944). S. Bradner and J. McQuaid.
Firewall Performance Measurement Techniques: A Scientific Approach. Marcus Ranum.
Warding Off the Cyberspace Invaders. Amy Cortese. Business Week. 03/13/95.
Vulnerability in Cisco Routers Used as Firewalls. Computer Incident Advisory Capability Advisory: Number D-15.
WAN-Hacking with AutoHack--Auditing Security behind the Firewall. Alec D.E. Muffett. Written by the author of Crack, the famous password-cracking program. Extraordinary document that deals with methods of auditing security from behind a firewall (and auditing of a network so large that it contained tens of thousands of hosts).
Windows NT Firewalls Are Born. PC Magazine. February 4, 1997.
IP v6 Release and Firewalls. Uwe Ellermann. 14th Worldwide Congress on Computer and Communications Security. Protection, pp. 341-354, June 1996.
The SunScreen Product Line Overview. Sun Microsystems.
Product Overview for IBM Internet Connection Secured Network Gateway for AIX, Version 2.2. IBM firewall information.
The Eagle Firewall Family. Raptor firewall information.
Secure Computing Firewall&tm; for NT. Overview. Secure Computing.
Check Point FireWall-1 Introduction. Check Point Technologies firewall information.
Cisco PIX Firewall. Cisco Systems firewall information.
Protecting the Fortress From Within and Without. R. Scott Raynovich. LAN Times. April 1996.
Internet Firewalls: An Introduction. Firewall white paper. NMI Internet Expert Services.
Features of the CentriTM Firewall. Centri firewall information.
Five Reasons Why an Application Gateway Is the Most Secure Firewall. Global Internet.
Back